Hi friends,
Yesterday, I hacked successfully the box Blue on Hack The Box site. This box is quite easy if you have the experience and feeling from the previous box: Legacy. We almost use the same technique from Legacy to compromise this Blue box. Let's get started:
First, we use nmap to scan for the open ports on that box: "nmap -T4 -p 1-65535 -A -sV 10.10.10.40". Do you see the port 445 is open? Then keep using nmap to check if there is any vulnerability on that port: "nmap --script vuln -p445 10.10.10.40"
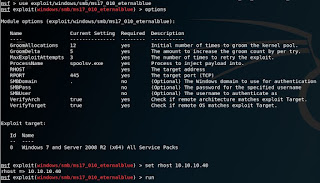
And, we will find that the box is vulnerable with MS17-010 bug. Now, we can use Metasploit to compromise it.
After using Metasploit, we will have the shell and can find the flags on the Desktop folder of user Administrator and haris.
If you want to go beyond the duty, you can do some forensics on that remote PC:
Happy hacking, my friends!



Comments
Post a Comment